Fortifying Digital Defenses: Exploring the Potential of Cybersecurity Mesh
Lately Digital acceleration in and around workplace, institutes has transformed what could be considered traditional network Infrastructures, challenges organisations face today are the rate at which digital transformation is accelerating adding to expanding attack surface, i.e., number of all possible points, exploitable by an unauthorized user to extract data or access system.
According to a study, pandemic-inspired shift to remote work requiring “Anywhere Operations” contributed to the growth of digital acceleration along with rise in IOT (Internet of things) technology. Other contributing technologies include Remote machines, Virtual networks, Cloud technologies, Edge computing devices. This transformation has leading organisations to invest more in cybersecurity mesh, i.e.,
Cybersecurity mesh is a modern approach to security architecture that allows enterprises to solve security problems arisen due to expanded attack surface caused by digital acceleration, hybrid multicloud architecture, distributed enterprises enabling scalability, flexibility, and reliable cybersecurity control. It’s a cyber-defence strategy independently securing devices with its own parameter
· As per the study, its projected cybersecurity mesh market to grow with CAGR of 18.4%, look at the Figure 1 for details-
· According to Gartner, by 2024, enterprises adopting cybersecurity mesh will reduce the financial impact by 90% due to the security incidents
· There has been continuous increase in the frequency of insider threats faced by companies compared to previous years, as per report 53% companies faced Insider threat in year 2018, that number rose to 60% in 2019 and 67% in 2020
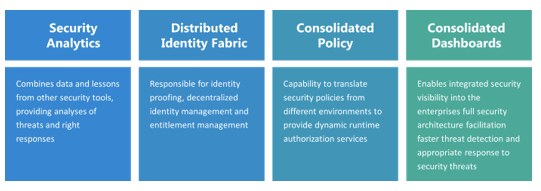
According to Gartner, below are the layers of CSMA (Cybersecurity Mesh Architecture), adopting the strategy provides advantages of composability, and scalability
Applications of Cybersecurity Mesh
Handling Majority of identity and IAM (access management Requests)-
Since the work from home has gained popularity, identities and devices exist outside the company premises, traditional cybersecurity doesn’t have required security measures to tackle such challenges, cybersecurity mesh is able to handle majority of IAM requests offering company a reliable digital asset and control approach. Cybersecurity mesh is predicted to support more than 50% of IAM requests
Managed Security Service providers (MSSP)-
According to report, by the year 2023, MSSP firms will be responsible for 40% of the IAM applications, they can provide companies with resources to plan, develop, acquire, and implement IAM Solutions as per there needs
Identity proofing tools-
With the continuous rise in remote interactions, it becomes difficult to identify between genuine valid users and an imposter. According to report, by the year 2024, 30% of large companies will implement new identity proofing tools addressing weaknesses in the workforce identity life cycle processes
Zero trust strategy-
Any device is by default not trusted to access the broader network as per Zero trust network. Threats can be detected in real time ensuring data, and systems are treated equally, unless verified by the security protocol, connection to data is considered by default “unreliable”
Decentralized identity standards-
Decentralized approach is emerging as a response to challenges faced by already established centralized approaches, with the help of block chain technology it protects anonymity and allows the individuals to validate information requests by providing them with least amount of information required. As per the report, a true decentralized standard will emerge by the year 2024
Challenges in the implementation of CSMA
Training and Support-
Being relatively new framework, it requires training and a change in mind-set, along with a significant amount of investment in personnel to support the transition. As well as ensuring simple identity-based system for the users without it being a distraction which could lead to reduced productivity
Associated Costs with an existing ecosystem-
Organisations with an existing security ecosystem might be hesitant to adopt CSMA, due to the incurred cost associated with implementing newer system based on a new approach, requiring significant time and mind-set change among the personnel’s
Conclusion-
Cybersecurity mesh is going to be the future of the digital security solutions, with larger number of companies adopting and implementing the system in their companies, MSSPs are continuously developing the system to better serve the organization’s needs
Implementation of this system is expected to bring demographic bias by focusing on document centric approaches as companies’ interest rise in the approach. Implementation of CSMA would require to overcome challenges of training and redefining cybersecurity perimeters, while providing flexible, scalable, reliable cybersecurity control and more standardization to security response approach.
Author: Abhishek Saini
