- Home
- About Us
- Industry
- Services
- Reading
- Contact Us
Threat Intelligence Management Market: Current Analysis and Forecast (2022-2030)
Emphasis on Component (Solution {Network, Risk, and Identity Management} and Services {Intelligence Feed and Threat Monitoring}); Deployment (On-Premises and Cloud); Enterprise Type (SME’s and Large Enterprises); Industry (BFSI, Retail & E-Commerce, Government & Defense, Healthcare, IT & Telecom, and Others); and Region/Country
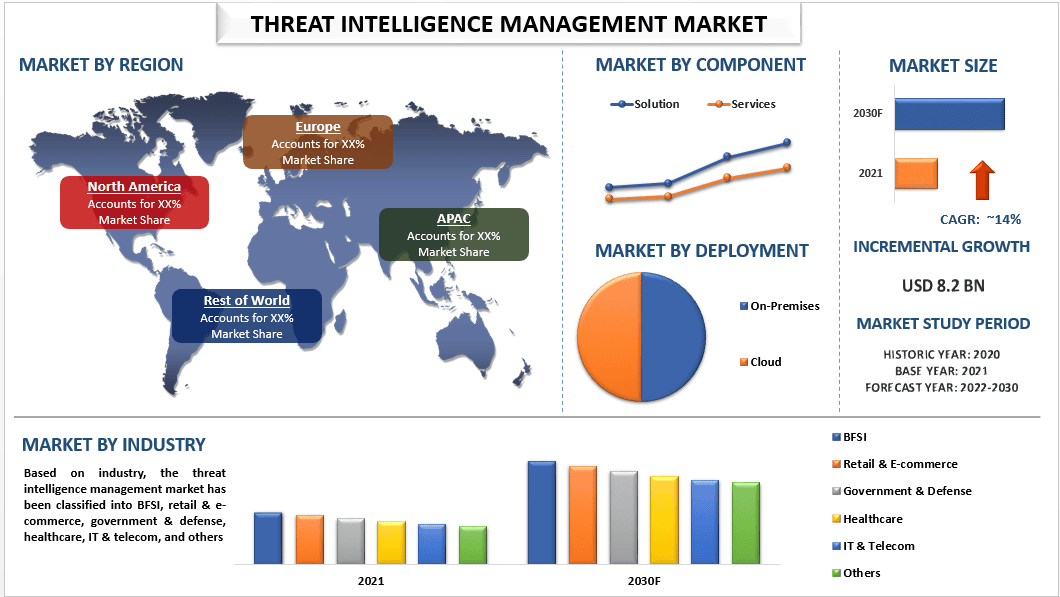
Global Threat Intelligence Management Market is expected to grow at a significant rate of around 14% during the forecast period. Threat Intelligence also known as cyber threat intelligence (CTI), is information gathered from a range of sources about current or potential attacks against an organization. The information is analyzed, refined, and organized and then used to minimize and mitigate cybersecurity risks. It is data and information about threats, threat intelligence management is the collection, normalization, enrichment, and actioning of data about potential attackers and their intentions, motivations, and capabilities. The main purpose of threat intelligence is to show organizations the various risks they face from external threats, such as zero-day threats and advanced persistent threats (APTs). Threat intelligence includes in-depth information and context about specific threats, such as who is attacking, their capabilities and motivation, and the indicators of compromise (IOCs). With this information, organizations can make informed decisions about how to defend against the most damaging attacks. For instance, in Apr 2023, Recorded Future launched an OpenAI GPT model for threat intel. The AI was trained on Recorded Future’s large data set and interprets evidence to help support enterprises struggling with cyber defense.
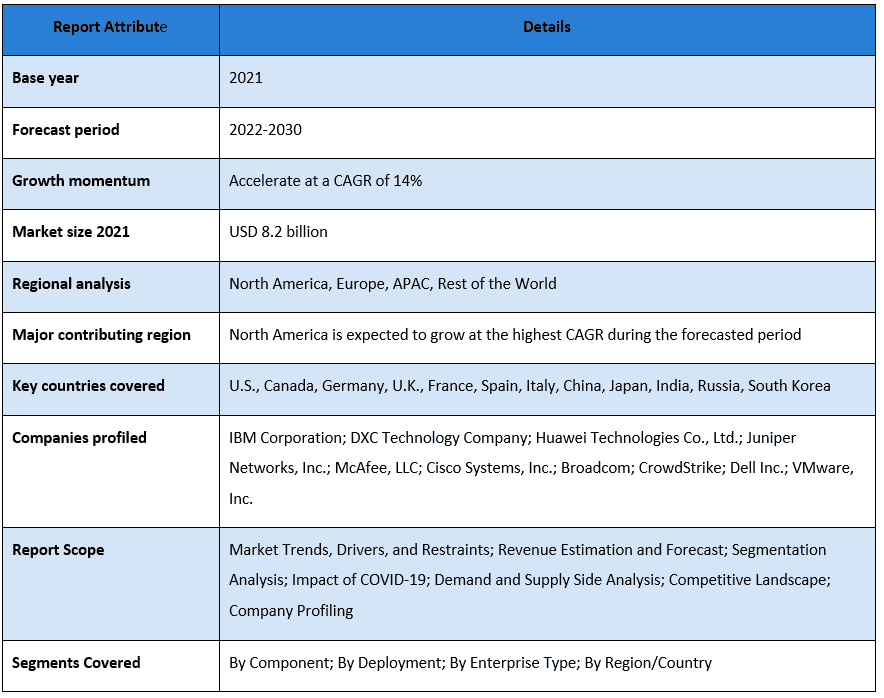
IBM Corporation; DXC Technology Company; Huawei Technologies Co., Ltd.; Juniper Networks, Inc.; McAfee, LLC; Cisco Systems, Inc.; Broadcom; CrowdStrike; Dell Inc.; VMware, Inc are some of the key players in the market. Several M&As along with partnerships have been undertaken by these players to facilitate customers with hi-tech and innovative products/technologies.
Insights Presented in the Report
“Amongst component, Solution category is expected to grow with a significant CAGR during the forecast period”
Based on component, the market is bifurcated into Solution {Network, Risk, and Identity Management} and Services {Intelligence Feed and Threat Monitoring}. The solution category is expected to grow with a significant CAGR during the forecast period. This is mainly owing to the becoming increasingly important in today’s digital age as organizations face an ever-evolving landscape of cyber threats. With the rise of sophisticated cyber-attacks, organizations need to be able to respond to potential threats quickly and effectively. Threat Intelligence Management enables organizations to collect, analyze, and disseminate threat intelligence information in a timely and efficient manner. This helps organizations identify potential threats, understand their sources and motives, and take proactive measures to mitigate them. Thus, the demand for threat intelligence management solutions is on the rise, as organizations seek to improve their cybersecurity posture and protect their critical assets.
“Amongst deployment, Cloud is expected to grow with a significant CAGR during the forecast period”
On the basis of deployment, the market is bifurcated into On-Premises and Cloud. Among these, the Cloud is expected to grow with a significant CAGR during the forecast period. This is mainly due to the increasingly popular as organizations move their data and applications to the cloud. The cloud provides organizations with greater flexibility, scalability, and cost-effectiveness, but it also introduces new security challenges. In addition, cloud-based threat intelligence management solutions help organizations to collect, analyze, and disseminate threat intelligence information in real-time, allowing them to quickly respond to potential threats. Additionally, cloud-based solutions offer centralized management, scalability, and reduced overhead costs, making them a more cost-effective option than on-premises solutions. Thus, the demand for cloud-based threat intelligence management solutions is increasing as organizations seek to improve their cybersecurity posture and protect their critical assets in the cloud.
Threat Intelligence Management Market Report Coverage
“North America is anticipated to grow at a substantial CAGR during the forecast period”
North America is anticipated to grow at a substantial CAGR during the forecast period. This is mainly owing to the most technologically advanced regions in the world and being home to many of the world’s leading organizations. Organizations face a high risk of cyber-attacks due to the large amount of sensitive data the companies handle and the sophisticated nature of cyber threats. The organizations collect, analyze, and disseminate threat intelligence information in real-time, allowing them to quickly respond to potential threats and minimize the impact of attacks. Additionally, the increasing regulatory focus on cybersecurity in North America, such as the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards, is driving the demand for advanced cybersecurity solutions like Threat Intelligence Management. Thus, the demand for threat intelligence management solutions in North America region is increasing as organizations seek to improve their cybersecurity posture and protect their critical assets.
Reasons to buy this report:
- The study includes market sizing and forecasting analysis validated by authenticated key industry experts.
- The report presents a quick review of overall industry performance at one glance.
- The report covers an in-depth analysis of prominent industry peers with a primary focus on key business financials, product portfolios, expansion strategies, and recent developments.
- Detailed examination of drivers, restraints, key trends, and opportunities prevailing in the industry.
- The study comprehensively covers the market across different segments.
- Deep dive regional level analysis of the industry.
Customization Options:
The global threat intelligence management market can further be customized as per the requirement or any other market segment. Besides this, UMI understands that you may have your own business needs, hence feel free to connect with us to get a report that completely suits your requirements.
Table of Content
Research Methodology for the Threat Intelligence Management Market Analysis (2022-2030)
Analyzing the historical market, estimating the current market, and forecasting the future market of the global threat intelligence management market were the three major steps undertaken to create and analyze the adoption of threat intelligence management in major regions globally. Exhaustive secondary research was conducted to collect the historical market numbers and estimate the current market size. Secondly, to validate these insights, numerous findings and assumptions were taken into consideration. Moreover, exhaustive primary interviews were also conducted, with industry experts across the value chain of the global threat intelligence management market. Post assumption and validation of market numbers through primary interviews, we employed a top-down/bottom-up approach to forecasting the complete market size. Thereafter, market breakdown and data triangulation methods were adopted to estimate and analyze the market size of segments and sub-segments of the industry pertains to. Detailed methodology is explained below:
Analysis of Historical Market Size
Step 1: In-Depth Study of Secondary Sources:
Detail secondary study was conducted to obtain the historical market size of the threat intelligence management market through company internal sources such as annual reports & financial statements, performance presentations, press releases, etc., and external sources including journals, news & articles, government publications, competitor publications, sector reports, third-party database, and other credible publications.
Step 2: Market Segmentation:
After obtaining the historical market size of the threat intelligence management market, we conducted a detailed secondary analysis to gather historical market insights and share for different segments & sub-segments for major regions. Major segments are included in the report as component, deployment, enterprise type, industry. Further country-level analyses were conducted to evaluate the overall adoption of testing models in that region.
Step 3: Factor Analysis:
After acquiring the historical market size of different segments and sub-segments, we conducted a detailed factor analysis to estimate the current market size of the threat intelligence management market. Further, we conducted factor analysis using dependent and independent variables such as various component, deployment, enterprise type, industry of web threat management. A thorough analysis was conducted for demand and supply-side scenarios considering top partnerships, mergers and acquisitions, business expansion, and product launches in the threat intelligence management market sector across the globe.
Current Market Size Estimate & Forecast
Current Market Sizing: Based on actionable insights from the above 3 steps, we arrived at the current market size, key players in the global threat intelligence management market, and market shares of the segments. All the required percentage shares split, and market breakdowns were determined using the above-mentioned secondary approach and were verified through primary interviews.
Estimation & Forecasting: For market estimation and forecast, weights were assigned to different factors including drivers & trends, restraints, and opportunities available for the stakeholders. After analyzing these factors, relevant forecasting techniques i.e., the top-down/bottom-up approach were applied to arrive at the market forecast for 2030 for different segments and sub-segments across the major markets globally. The research methodology adopted to estimate the market size encompasses:
- The industry’s market size, in terms of revenue (USD) and the adoption rate of the threat intelligence management market across the major markets domestically
- All percentage shares, splits, and breakdowns of market segments and sub-segments
- Key players in the global threat intelligence management market in terms of products offered. Also, the growth strategies adopted by these players to compete in the fast-growing market
Market Size and Share Validation
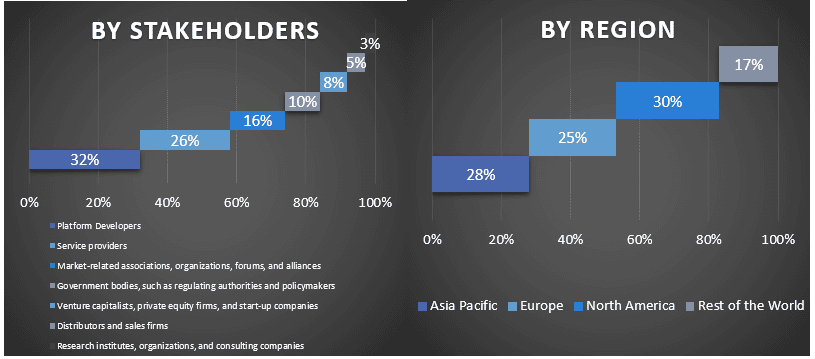
Primary Research: In-depth interviews were conducted with the Key Opinion Leaders (KOLs) including Top Level Executives (CXO/VPs, Sales Head, Marketing Head, Operational Head, Regional Head, Country Head, etc.) across major regions. Primary research findings were then summarized, and statistical analysis was performed to prove the stated hypothesis. Inputs from primary research were consolidated with secondary findings, hence turning information into actionable insights.
Split of Primary Participants in Different Regions
Market Engineering
The data triangulation technique was employed to complete the overall market estimation and to arrive at precise statistical numbers for each segment and sub-segment of the global threat intelligence management market. Data was split into several segments & sub-segments post studying various parameters and trends in the areas of component, deployment, enterprise type, industry in the global threat intelligence management market.
The main objective of the Global Threat intelligence management Market Study
The current & future market trends of the global threat intelligence management market were pinpointed in the study. Investors can gain strategic insights to base their discretion for investments on the qualitative and quantitative analysis performed in the study. Current and future market trends determined the overall attractiveness of the market at a regional level, providing a platform for the industrial participant to exploit the untapped market to benefit from a first-mover advantage. Other quantitative goals of the studies include:
- Analyze the current and forecast market size of the threat intelligence management market in terms of value (USD). Also, analyze the current and forecast market size of different segments and sub-segments
- Segments in the study include areas of component, deployment, enterprise type, industry.
- Define and analysis of the regulatory framework for the threat intelligence management
- Analyze the value chain involved with the presence of various intermediaries, along with analyzing customer and competitor behaviors of the industry.
- Analyze the current and forecast market size of the threat intelligence management market for the major region.
- Major countries of regions studied in the report include Asia Pacific, Europe, North America, and the Rest of the World.
- Company profiles of the threat intelligence management market and the growth strategies adopted by the market players to sustain in the fast-growing market
- Deep dive regional level analysis of the industry
Related Reports
Customers who bought this item also bought










